Settings
The AppBase encoder is critical in ensuring the security and integrity of user responses. AppBase proactively protects your application against Cross-Site Scripting (XSS) attacks by employing robust encoding techniques.
XSS vulnerabilities arise when malicious JavaScript or HTML code is inadvertently or intentionally injected into a rule response. This injected code can then be executed by the user's browser, potentially leading to a range of harmful consequences, including:
- Data theft: Attackers can steal sensitive information, such as login credentials or session cookies.
- Website defacement: Attackers can alter the appearance and content of your website.
- Redirects to malicious websites: Attackers can redirect users to websites that contain malware or phishing scams.
- Account takeover: Attackers can gain control of user accounts.
The AppBase encoder addresses this threat by scrutinizing rule outputs before reaching the user's browser.
This "encoder" technology efficiently removes or replaces any potentially dangerous JS or HTML code, thereby neutralizing the threat posed by XSS attacks.
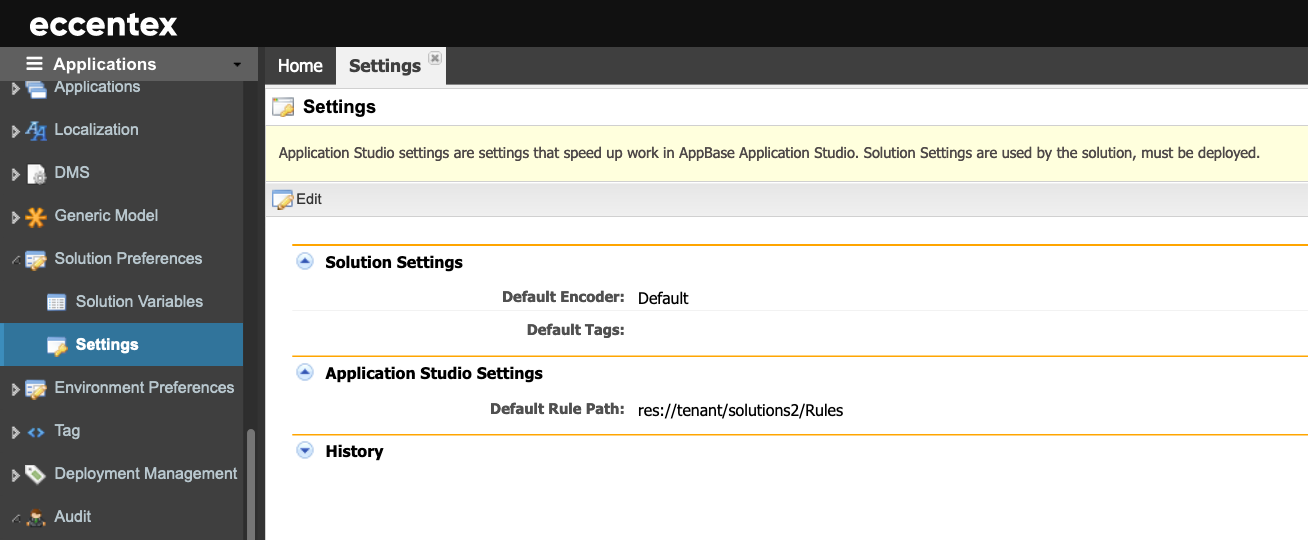
Steps
On the top right, navigate to → Application Studio → <<solution>>
- Navigate to → from the left-hand navigation menu.
- Click the Edit button to modify the default settings.
- Select or modify the Default Encoder from the list of supported encoders (see table below for more details).
- Specify the Default Rule Path where the rules will be saved.
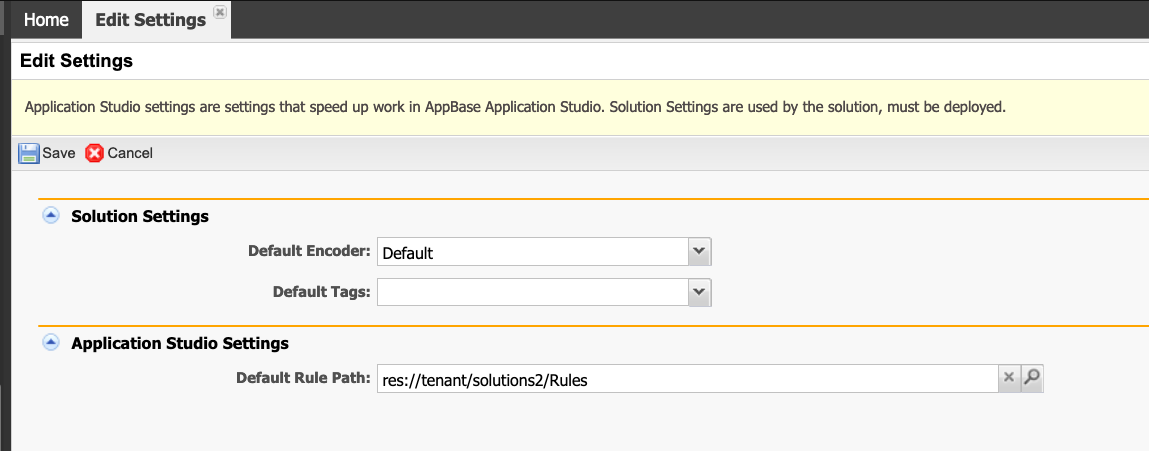
- Click Save to commit your changes or Cancel to exit without saving.
Supported Encoders
This table provides a list of supported encoders with an output example for the parameter added by this code example.
| Encoder Name | Description | Output Example |
|---|---|---|
| None | No output encoder is used. The output is not modified and returned as is. Use to turn off the output encoding. It does not protect against XSS attacks. | {"DATA":{"root_Enc_CSharp":{"Parameter1":"<div onclick=\"alert('test');\">javascript1</div>","ValidationSummary":{"VALIDATION":null,"IsValid":true}}}} |
| Html Sanitizer | Default AppBase output encoder. The output is modified and sanitized. The safe HTML is kept, and any dangerous HTML formatting is removed. It provides moderate protection against XSS attacks, which is probably enough for most situations. This is the only HTML Sanitizer available in AppBase, all other output encoders are encoders that removes or encode the HTML formatting. The difference between encoding and sanitizing is that the latter keeps some safe HTML while the former aims to encode/remove all HTML formatting. | {"DATA":{"root_Enc_CSharp":{"Parameter1":"","ValidationSummary":{"VALIDATION":null,"IsValid":true}}}} |
| Microsoft Sanitizer Html Fragment | Encodes output using Microsoft.Security.Application.Sanitizer.GetSafeHtmlFragment method | {"DATA":{"root_Enc_CSharp":{"Parameter1":"javascript1","ValidationSummary":{"VALIDATION":null,"IsValid":true}}}} |
| Microsoft AntiXSS Html Encoder | It is one of the strictest encoders, which provides one of the best protections against XSS attacks by encoding all unsafe characters. Uses Microsoft.Security.Application.Encoder.HtmlEncode to encode the output. | {"DATA":{"root_Enc_CSharp":{"Parameter1":"<div onclick="alert('test');">javascript1</div>","ValidationSummary":{"VALIDATION":null,"IsValid":true}}}} |
| Html Encode | Wrapper to System.Web.HttpUtility.HtmlEncode method. It provides results similar to "Microsoft AntiXSS Html Encoder" but is probably less secure than "Microsoft AntiXSS Html Encoder." |
|

